Kevin Mathew is an IT professional specializing in Customer Identity and Access Management (CIAM). With extensive experience in enhancing digital security and user experience, he drives innovation and efficiency in identity management solutions.
-
53 Beiträge
-
39 Fotos
-
0 Videos
-
28/04/1995
-
anschliessend 0 people
© 2024 hallbook | Rede Social Brasileira
 Deutsch
Deutsch
Jüngste Beiträge
-
How to Build a Functional Telegram Bot: A Complete Overview
In "How to Build a Functional Telegram Bot: A Complete Overview," you'll learn how to make a Telegram bot from scratch. This guide covers essential steps, including setting up your bot with the BotFather, understanding the Telegram API, and writing code to implement various functionalities. By the end, you'll have a fully operational bot ready to interact with users and perform tasks, empowering you to enhance your Telegram experience with automation and engagement.
More Info - https://www.loginradius.com/blog/engineering/how-to-make-telegram-bot/How to Build a Functional Telegram Bot: A Complete Overview In "How to Build a Functional Telegram Bot: A Complete Overview," you'll learn how to make a Telegram bot from scratch. This guide covers essential steps, including setting up your bot with the BotFather, understanding the Telegram API, and writing code to implement various functionalities. By the end, you'll have a fully operational bot ready to interact with users and perform tasks, empowering you to enhance your Telegram experience with automation and engagement. More Info - https://www.loginradius.com/blog/engineering/how-to-make-telegram-bot/0 Kommentare 0 Anteile 134 Ansichten 0 VorschauPlease log in to like, share and comment! -
PHP API Security: Implementing JWT for Authentication
PHP API Security is crucial for protecting your application from unauthorized access. Implementing JSON Web Tokens (JWT) for authentication enhances this security by allowing you to verify user identities securely. JWTs provide a compact, URL-safe means of representing claims, enabling stateless authentication and protecting sensitive data. This guide walks you through the steps to integrate JWT into your PHP API, ensuring robust authentication while maintaining a seamless user experience.
More Info - https://www.loginradius.com/blog/engineering/guest-post/securing-php-api-with-jwt/PHP API Security: Implementing JWT for Authentication PHP API Security is crucial for protecting your application from unauthorized access. Implementing JSON Web Tokens (JWT) for authentication enhances this security by allowing you to verify user identities securely. JWTs provide a compact, URL-safe means of representing claims, enabling stateless authentication and protecting sensitive data. This guide walks you through the steps to integrate JWT into your PHP API, ensuring robust authentication while maintaining a seamless user experience. More Info - https://www.loginradius.com/blog/engineering/guest-post/securing-php-api-with-jwt/0 Kommentare 0 Anteile 132 Ansichten 0 Vorschau -
Secure Your Online Presence: Setting Up Two-Factor Authentication
In today's digital landscape, securing your online accounts is crucial. This guide will help you understand how to set up two-factor authentication (2FA) across various platforms, enhancing your account security significantly. By requiring a second form of verification, 2FA adds an extra layer of protection against unauthorized access. Follow our easy steps to set up two-factor authentication and safeguard your online presence effectively.
More Info - https://www.loginradius.com/blog/identity/how-to-setup-2fa-in-online-accounts/Secure Your Online Presence: Setting Up Two-Factor Authentication In today's digital landscape, securing your online accounts is crucial. This guide will help you understand how to set up two-factor authentication (2FA) across various platforms, enhancing your account security significantly. By requiring a second form of verification, 2FA adds an extra layer of protection against unauthorized access. Follow our easy steps to set up two-factor authentication and safeguard your online presence effectively. More Info - https://www.loginradius.com/blog/identity/how-to-setup-2fa-in-online-accounts/0 Kommentare 0 Anteile 77 Ansichten 0 Vorschau -
Implementing Secure User Authentication in Flutter: Signup and Login
Learn how to implement secure Flutter Authentication for user signup and login in your app. This guide covers essential steps like form validation, password encryption, and API integration to ensure robust security. Enhance your Flutter app with effective authentication features that protect user data and provide a seamless login experience.
More Info - https://www.loginradius.com/blog/engineering/guest-post/authenticating-flutter-apps/Implementing Secure User Authentication in Flutter: Signup and Login Learn how to implement secure Flutter Authentication for user signup and login in your app. This guide covers essential steps like form validation, password encryption, and API integration to ensure robust security. Enhance your Flutter app with effective authentication features that protect user data and provide a seamless login experience. More Info - https://www.loginradius.com/blog/engineering/guest-post/authenticating-flutter-apps/0 Kommentare 0 Anteile 173 Ansichten 0 Vorschau -
Cookieless Authentication vs. Cookie-Based: Which is More Secure?
In "Cookieless Authentication vs. Cookie-Based: Which is More Secure?", we explore the security implications of cookie-based vs. cookieless authentication methods. Discover how each approach handles user data, mitigates threats, and ensures privacy. This insightful comparison will help you understand the strengths and weaknesses of both authentication styles, guiding you toward the most secure option for your applications.
More Info - https://www.loginradius.com/blog/engineering/cookie-based-vs-cookieless-authentication/Cookieless Authentication vs. Cookie-Based: Which is More Secure? In "Cookieless Authentication vs. Cookie-Based: Which is More Secure?", we explore the security implications of cookie-based vs. cookieless authentication methods. Discover how each approach handles user data, mitigates threats, and ensures privacy. This insightful comparison will help you understand the strengths and weaknesses of both authentication styles, guiding you toward the most secure option for your applications. More Info - https://www.loginradius.com/blog/engineering/cookie-based-vs-cookieless-authentication/0 Kommentare 0 Anteile 169 Ansichten 0 Vorschau -
Top Hacking Tools and How LoginRadius Enhances Security
Discover the best hacking tools used by cybercriminals and learn how LoginRadius enhances your security to protect against these threats. This guide explores top hacking tools and highlights how LoginRadius provides robust authentication, multi-factor security, and real-time threat detection to keep your data safe from potential breaches. Stay protected with advanced security measures!
More Info - https://www.loginradius.com/blog/engineering/best-hacking-tools/Top Hacking Tools and How LoginRadius Enhances Security Discover the best hacking tools used by cybercriminals and learn how LoginRadius enhances your security to protect against these threats. This guide explores top hacking tools and highlights how LoginRadius provides robust authentication, multi-factor security, and real-time threat detection to keep your data safe from potential breaches. Stay protected with advanced security measures! More Info - https://www.loginradius.com/blog/engineering/best-hacking-tools/0 Kommentare 0 Anteile 148 Ansichten 0 Vorschau -
Build a Custom Login/Signup UI with Tailwind CSS and React
Learn how to create a custom Login/Signup form using Tailwind CSS and React. This guide will walk you through building a sleek, responsive user interface that is easy to implement and customize. Tailwind CSS offers utility-first classes for fast styling, while React enables efficient component-based development. Together, they provide a powerful solution for developing modern authentication forms that enhance both design and functionality.
More Info - https://www.loginradius.com/blog/engineering/guest-post/modern-login-signup-form-tailwindcss-react/Build a Custom Login/Signup UI with Tailwind CSS and React Learn how to create a custom Login/Signup form using Tailwind CSS and React. This guide will walk you through building a sleek, responsive user interface that is easy to implement and customize. Tailwind CSS offers utility-first classes for fast styling, while React enables efficient component-based development. Together, they provide a powerful solution for developing modern authentication forms that enhance both design and functionality. More Info - https://www.loginradius.com/blog/engineering/guest-post/modern-login-signup-form-tailwindcss-react/0 Kommentare 0 Anteile 157 Ansichten 0 Vorschau -
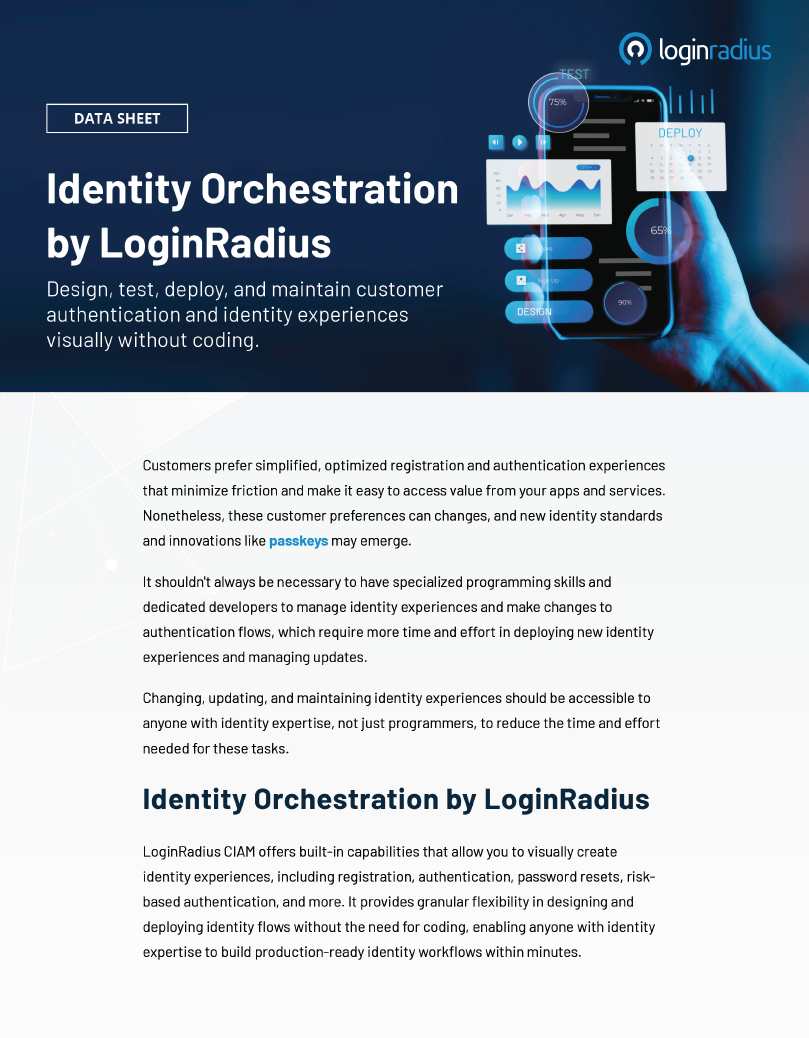
Optimize Identity Management with LoginRadius Orchestration
Optimize your identity management processes with LoginRadius Identity Orchestration. This solution seamlessly integrates various authentication methods, streamlines user identity flows, and ensures a secure, unified experience across platforms. By automating complex identity tasks, Identity Orchestration enhances security, reduces friction for users, and simplifies management for businesses. Whether it's multi-factor authentication, social login, or single sign-on, LoginRadius provides a flexible and scalable approach to modern identity management.
More Info - https://www.loginradius.com/resource/datasheet/identity-orchestration-workflow/Optimize Identity Management with LoginRadius Orchestration Optimize your identity management processes with LoginRadius Identity Orchestration. This solution seamlessly integrates various authentication methods, streamlines user identity flows, and ensures a secure, unified experience across platforms. By automating complex identity tasks, Identity Orchestration enhances security, reduces friction for users, and simplifies management for businesses. Whether it's multi-factor authentication, social login, or single sign-on, LoginRadius provides a flexible and scalable approach to modern identity management. More Info - https://www.loginradius.com/resource/datasheet/identity-orchestration-workflow/0 Kommentare 0 Anteile 148 Ansichten 0 Vorschau -
LoginRadius: How to Implement OpenID Connect for Single Sign-On
Learn how to implement OpenID Connect for Single Sign-On (SSO) with LoginRadius in this step-by-step guide. OpenID Connect simplifies user authentication, allowing seamless login experiences across multiple platforms. By integrating LoginRadius with OpenID Connect, you can enhance security and streamline access for your users, ensuring a secure and efficient SSO process.
More Info - https://www.loginradius.com/blog/engineering/implementing-oidc-sso-loginradius-as-identity-provider/LoginRadius: How to Implement OpenID Connect for Single Sign-On Learn how to implement OpenID Connect for Single Sign-On (SSO) with LoginRadius in this step-by-step guide. OpenID Connect simplifies user authentication, allowing seamless login experiences across multiple platforms. By integrating LoginRadius with OpenID Connect, you can enhance security and streamline access for your users, ensuring a secure and efficient SSO process. More Info - https://www.loginradius.com/blog/engineering/implementing-oidc-sso-loginradius-as-identity-provider/0 Kommentare 0 Anteile 131 Ansichten 0 Vorschau -
How Chrome’s Cookie Policy Changes Influence Authentication Methods
Chrome's recent cookie policy changes, including the introduction of chrome partitioned cookies, significantly impact user authentication methods. By isolating cookies to specific sites, these changes enhance privacy but can disrupt traditional authentication flows that rely on third-party cookies. This shift requires adapting authentication strategies to ensure seamless user experiences while maintaining security. Organizations must explore alternative solutions, such as first-party cookies or token-based methods, to navigate the new landscape of authentication influenced by Chrome’s policy updates.
More Info - https://www.loginradius.com/blog/engineering/identity-impact-of-google-chrome-thirdparty-cookie-restrictions/How Chrome’s Cookie Policy Changes Influence Authentication Methods Chrome's recent cookie policy changes, including the introduction of chrome partitioned cookies, significantly impact user authentication methods. By isolating cookies to specific sites, these changes enhance privacy but can disrupt traditional authentication flows that rely on third-party cookies. This shift requires adapting authentication strategies to ensure seamless user experiences while maintaining security. Organizations must explore alternative solutions, such as first-party cookies or token-based methods, to navigate the new landscape of authentication influenced by Chrome’s policy updates. More Info - https://www.loginradius.com/blog/engineering/identity-impact-of-google-chrome-thirdparty-cookie-restrictions/0 Kommentare 0 Anteile 188 Ansichten 0 Vorschau
Mehr Artikel