Data-Centric Security Market Outlook and Growth Prospects
Data-Centric Security 2024
In today's digital age, data is often referred to as the "new oil." As organizations increasingly rely on data to drive their operations and decision-making, protecting this valuable asset has never been more critical. Traditional security models, which focus primarily on perimeter defenses, are becoming inadequate in the face of sophisticated cyber threats. This is where data-centric security comes into play. Data-centric security emphasizes the protection of data itself, regardless of where it resides or how it is accessed. The Data-Centric Security Market Share reflects this shift, showcasing the growing recognition of the need for more robust data protection mechanisms.
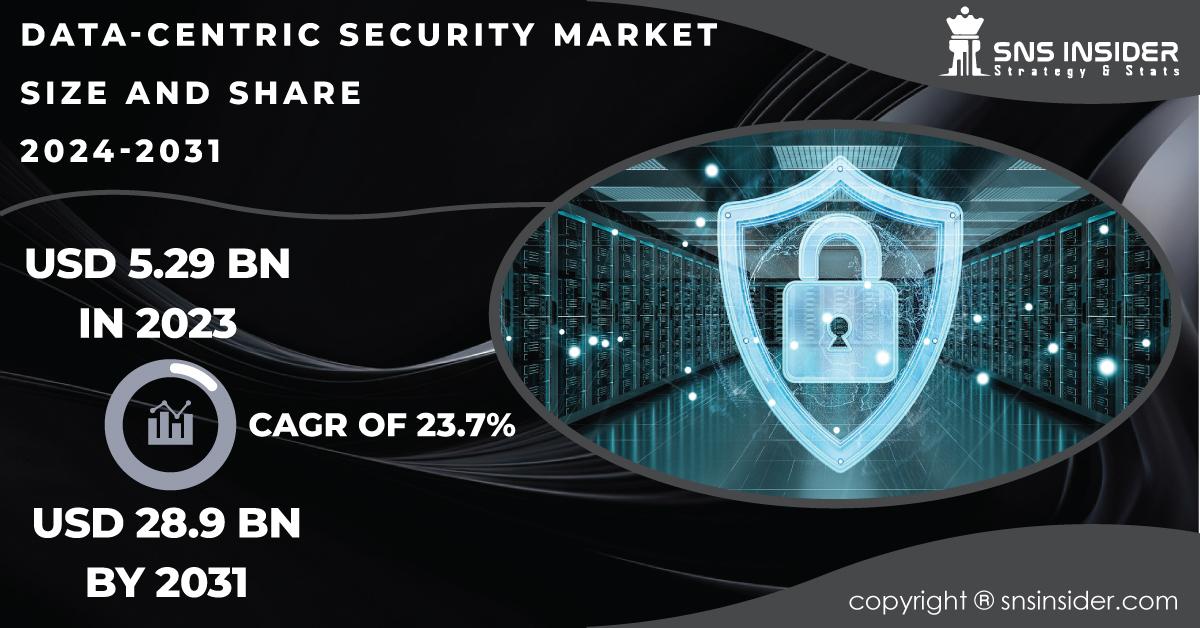
The Data-Centric Security Market Size was valued at USD 5.29 billion in 2023 and is expected to reach USD 28.9 billion by 2031, growing at a CAGR of 23.7% over the forecast period from 2024 to 2031. This remarkable growth is driven by several factors, including the increasing volume of data generated, rising regulatory compliance requirements, and the growing frequency of data breaches.
Understanding Data-Centric Security
Data-centric security is a comprehensive approach that focuses on protecting data throughout its lifecycle—from creation and storage to usage and disposal. Unlike traditional security measures that primarily target network and endpoint security, data-centric security recognizes that the data itself is the most critical asset to safeguard. This approach encompasses various strategies, including data encryption, access controls, data masking, and activity monitoring.
One of the core principles of data-centric security is the concept of data classification. Organizations must identify and categorize their data based on its sensitivity and importance. Sensitive data, such as personally identifiable information (PII), financial records, and intellectual property, requires more stringent protection measures compared to less sensitive information. By classifying data, organizations can implement tailored security measures that align with the specific risks associated with each category.
The Role of Encryption in Data-Centric Security
Encryption is a fundamental component of data-centric security. It transforms readable data into an unreadable format, ensuring that only authorized users with the appropriate decryption keys can access it. By encrypting sensitive data, organizations can protect it from unauthorized access, even if it falls into the wrong hands. This is particularly important in today's landscape, where data breaches are increasingly common.
There are various encryption methods available, including symmetric and asymmetric encryption. Symmetric encryption uses the same key for both encryption and decryption, while asymmetric encryption relies on a pair of keys: a public key for encryption and a private key for decryption. Organizations must choose the appropriate encryption method based on their specific use cases and security requirements.
In addition to encryption, organizations must also consider data in transit. Data can be vulnerable while being transmitted across networks, making it essential to implement secure communication protocols such as Transport Layer Security (TLS) to protect data during transmission. This multi-layered approach ensures that data remains secure at all stages of its lifecycle.
Access Controls: Restricting Who Can See the Data
Another critical aspect of data-centric security is access control. Organizations must implement robust access control mechanisms to ensure that only authorized personnel can access sensitive data. This involves setting up role-based access controls (RBAC) that define user roles and permissions based on their responsibilities within the organization.
Identity and access management (IAM) solutions play a vital role in enforcing access controls. These solutions allow organizations to manage user identities, authenticate users, and monitor access to sensitive data. Multi-factor authentication (MFA) is another essential security measure that adds an additional layer of protection by requiring users to provide multiple forms of verification before gaining access.
Additionally, organizations should conduct regular access reviews to ensure that user permissions are up to date. This is particularly important in large organizations where employee roles may change frequently. By regularly auditing access controls, organizations can identify and revoke access for users who no longer require it, thereby reducing the risk of unauthorized access.
Data Masking: Protecting Sensitive Information
Data masking is a technique used to protect sensitive information by replacing it with fictional data that retains the original format but does not reveal the actual content. This is particularly useful in non-production environments, such as software testing or development, where real data is not necessary.
By using data masking, organizations can ensure that sensitive information is not exposed during testing or training processes. For example, instead of using real customer names and addresses, organizations can use fictitious data that maintains the same structure. This allows developers and testers to work with realistic data sets while safeguarding sensitive information from potential breaches.
Data masking can also be applied in scenarios where data is shared with third parties. By masking sensitive data before sharing, organizations can collaborate with partners and vendors without exposing their proprietary information. This fosters trust and security in business relationships while adhering to data protection regulations.
Compliance and Regulatory Considerations
With the increasing focus on data protection, organizations must navigate a complex landscape of regulatory requirements. Regulations such as the General Data Protection Regulation (GDPR), the Health Insurance Portability and Accountability Act (HIPAA), and the California Consumer Privacy Act (CCPA) impose strict requirements on how organizations handle and protect sensitive data.
Data-centric security plays a crucial role in ensuring compliance with these regulations. By implementing robust data protection measures, organizations can demonstrate their commitment to safeguarding personal information and fulfilling their legal obligations. Failure to comply with these regulations can result in severe penalties, reputational damage, and loss of customer trust.
Organizations must conduct regular assessments to ensure compliance with applicable regulations. This includes identifying the types of data they collect, how it is processed, and the security measures in place to protect it. By maintaining transparency and accountability, organizations can mitigate the risks associated with non-compliance.
The Growing Threat Landscape
The rise in cyber threats has made data-centric security more critical than ever. Cybercriminals are constantly evolving their tactics, employing sophisticated techniques to breach security defenses and access sensitive data. High-profile data breaches have highlighted the vulnerabilities in traditional security models and the need for a proactive approach to data protection.
Ransomware attacks, in particular, have surged in recent years, with attackers targeting organizations of all sizes. By encrypting critical data and demanding ransom payments for decryption keys, cybercriminals can disrupt operations and cause significant financial losses. Data-centric security measures, such as robust encryption and access controls, can help organizations mitigate the risks associated with ransomware attacks.
Additionally, insider threats pose a significant risk to organizations. Employees with access to sensitive data can intentionally or unintentionally expose it, leading to data breaches. By implementing strict access controls and monitoring user activities, organizations can detect and respond to suspicious behavior, thereby reducing the likelihood of insider threats.
The Future of Data-Centric Security
As organizations continue to embrace digital transformation, the importance of data-centric security will only increase. The proliferation of cloud computing, Internet of Things (IoT) devices, and big data analytics presents new challenges for data protection. Organizations must adopt a proactive approach to security, focusing on protecting data at its core.
Emerging technologies, such as artificial intelligence (AI) and machine learning (ML), offer exciting opportunities for enhancing data-centric security. These technologies can analyze vast amounts of data to identify anomalies, detect potential threats, and automate security responses. By leveraging AI and ML, organizations can stay one step ahead of cybercriminals and strengthen their data protection measures.
Additionally, as organizations continue to adopt hybrid and multi-cloud environments, they must ensure that their data-centric security strategies extend across all platforms. This requires a unified approach that encompasses on-premises, cloud, and edge environments to protect data regardless of where it resides.
Conclusion
In conclusion, data-centric security represents a fundamental shift in how organizations approach data protection. By focusing on safeguarding data itself, organizations can better mitigate the risks associated with cyber threats and regulatory compliance. With the rapid growth of the Data-Centric Security Market, it is clear that businesses are recognizing the need for more robust and proactive security measures. As the digital landscape continues to evolve, embracing data-centric security will be essential for organizations seeking to protect their most valuable asset: their data.
Contact Us:
Akash Anand – Head of Business Development & Strategy
info@snsinsider.com
Phone: +1-415-230-0044 (US) | +91-7798602273 (IND)
About Us
SNS Insider is one of the leading market research and consulting agencies that dominates the market research industry globally. Our company's aim is to give clients the knowledge they require in order to function in changing circumstances. In order to give you current, accurate market data, consumer insights, and opinions so that you can make decisions with confidence, we employ a variety of techniques, including surveys, video talks, and focus groups around the world.
Read Our Other Reports:
Sales Training Software Market Share
- Data-Centric_Security_Market
- Data-Centric_Security_Market_Size
- Data-Centric_Security_Market_Share
- Data-Centric_Security_Market_Growth
- Data-Centric_Security_Market_Trends
- Data-Centric_Security_Market_Report
- Data-Centric_Security_Market_Analysis
- Data-Centric_Security_Market_Forecast
- Data-Centric_Security_Industry
- Data-Centric_Security_Market_Research
- Art
- Causes
- Crafts
- Dance
- Drinks
- Film
- Fitness
- Food
- Giochi
- Gardening
- Health
- Home
- Literature
- Music
- Networking
- Altre informazioni
- Party
- Religion
- Shopping
- Sports
- Theater
- Wellness


