Спонсоры
Cybersecurity Threats: A Complete Breakdown
As our lives become increasingly digital, the importance of cybersecurity cannot be overstated. Cybersecurity threats pose serious risks to individuals, businesses, and even nations. Understanding these threats is crucial for developing effective strategies to protect sensitive information and maintain the integrity of our digital systems. This blog provides a complete breakdown of the various cybersecurity threats we face today.
If you want to excel in this career path, then it is recommended that you upgrade your skills and knowledge regularly with the latest Cyber Security Online Training.

What Are Cybersecurity Threats?
Cybersecurity threats refer to any potential danger that can compromise the confidentiality, integrity, or availability of information and systems. These threats can arise from various sources, including malicious actors, insider threats, and even technological vulnerabilities. By identifying and understanding these threats, we can better prepare to defend against them.
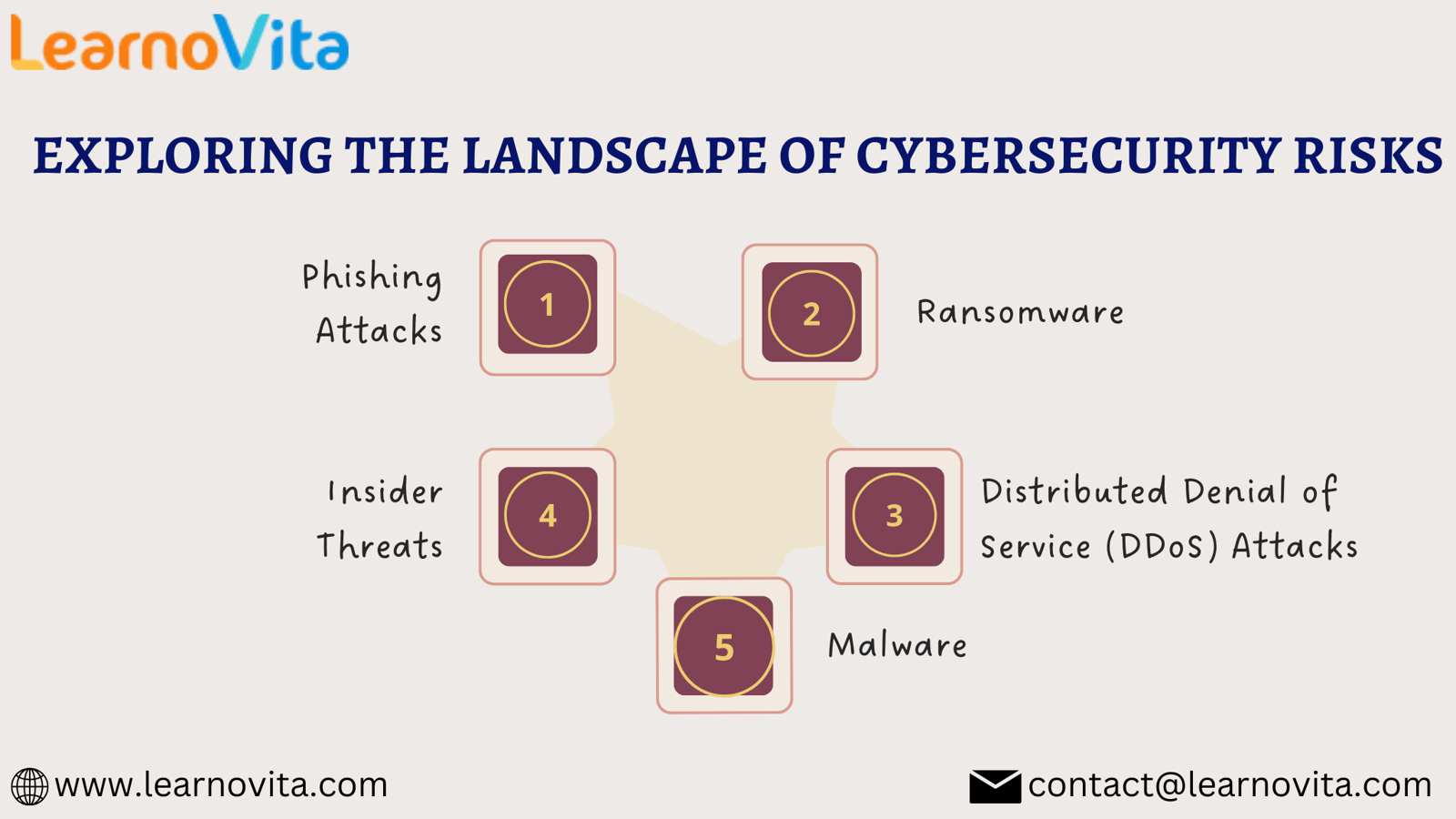
Major Types of Cybersecurity Threats
1. Phishing Attacks
Phishing attacks are one of the most common and effective methods used by cybercriminals. In these attacks, fraudsters send deceptive emails or messages that appear to be from legitimate sources. The goal is to trick recipients into revealing sensitive information, such as login credentials or financial details.
Protective Measures:
- Always verify the sender’s email address before clicking on links or downloading attachments.
- Be cautious of emails that create a sense of urgency or ask for personal information.
- Implement advanced email filtering solutions to detect and block phishing attempts.
2. Ransomware
Ransomware is a type of malware that encrypts a victim's files, making them inaccessible until a ransom is paid. This form of attack can paralyze organizations and lead to significant financial losses and operational disruptions.
Protective Measures:
- Regularly back up important data to an offline or secure location.
- Keep software and operating systems updated to protect against known vulnerabilities.
- Educate employees about safe browsing habits and how to recognize potential ransomware attacks.
3. Malware
Malware includes a broad range of malicious software designed to infiltrate and damage computer systems. This category encompasses viruses, worms, trojans, and spyware, each with unique methods of attack.
Protective Measures:
- Install reputable antivirus and anti-malware software and keep it updated.
- Avoid downloading files or software from untrusted or unknown sources.
- Regularly update all software to close security gaps.
With the aid of Best Software Training Institute programs, which offer comprehensive training and job placement support to anyone looking to develop their talents, it’s easier to learn this tool and advance your career.
4. Insider Threats
Insider threats come from individuals within an organization—such as employees, contractors, or business partners—who may intentionally or unintentionally compromise security. This can include leaking sensitive information or neglecting security protocols.
Protective Measures:
- Implement strict access controls to limit sensitive data exposure.
- Monitor user activity and conduct regular security training for employees.
- Foster a culture of accountability and transparency to reduce the likelihood of insider threats.
5. Distributed Denial of Service (DDoS) Attacks
DDoS attacks flood a target’s systems with excessive traffic, overwhelming them and rendering services unavailable to legitimate users. These attacks can disrupt business operations and lead to significant downtime.
Protective Measures:
- Utilize traffic monitoring tools to detect unusual spikes in activity.
- Invest in DDoS mitigation services to absorb and filter malicious traffic.
- Develop an incident response plan to address potential DDoS attacks quickly.
Conclusion
Cybersecurity threats pose significant risks in our increasingly digital world. By breaking down the various types of threats and understanding their implications, individuals and organizations can take proactive measures to protect their sensitive information and systems. Regular training, vigilance, and a robust security posture are essential for navigating the complexities of cybersecurity. Staying informed and prepared is the best defense against the ever-evolving risks in our interconnected landscape.
Категории
Больше
When it comes to upgrading your home, Double Glazing Doors are an essential feature that combines practicality with elegance. At UK Double Glazed, we provide top-quality double glazing solutions designed to enhance energy efficiency, security, and the aesthetic appeal of your property. Whether you’re renovating or building a new home, double glazing doors offer numerous benefits that make...

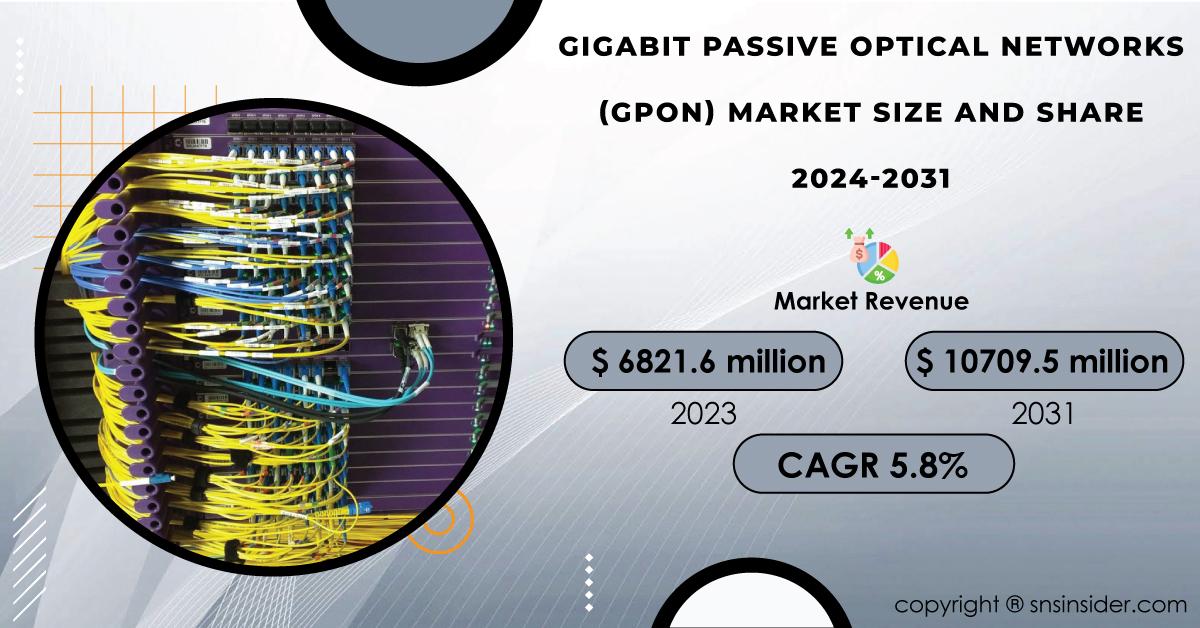
Gigabit Passive Optical Networks Industry Scope and Overview The latest market report released offers a comprehensive analysis of the Gigabit Passive Optical Networks Industry. This report delves deep into the intricacies of the market, providing stakeholders with invaluable insights into competitive landscapes, market segmentation, regional outlooks, and the impact of global events. In...